考点:代码审计、正则绕过、basename缺陷
打开
1 | <?php |
分析
题目直接给出了源代码,通过分析,可以得到两段代码。先看看下半段。
1 | # 随机生成64位二进制字节,再转换位十六进制 赋值给$secret |
这段代码,是想让我们传入字符串,要求字符串与随机生成的字符串一样,那么才会输出flag。几乎不太可能。
分析上半段代码。
1 | # $_SERVER['PHP_SELF'] 是获取url中域名后边的部分 www.xxx.com/index.php/config.php 就是获取 index.php/config.php |
如果通过highlight_file去读取config.php 文件,这段代码看起来好像是不太行,通过传入 /index.php/config.php 会被正则直接拦下来。但是basename 这个函数有个小小的问题,就是文件名首尾任何非ASCII码的字符都会被rename函数删除掉。官网https://bugs.php.net/bug.php?id=62119。
1 | $path='/test/äaä.txt'; |
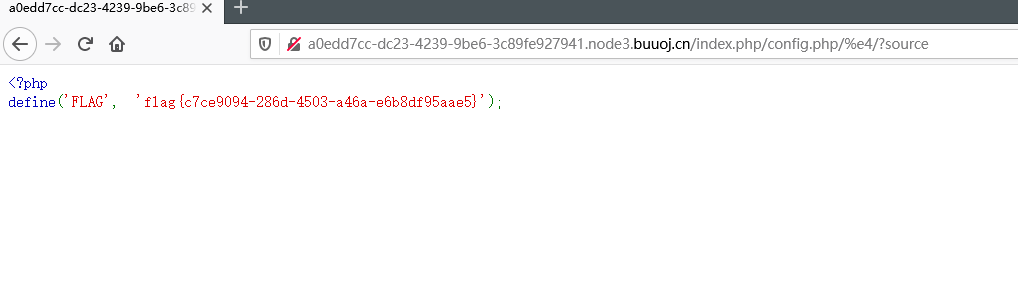
构造payload
1 | /index.php/config.php/%e4/?source |
首先浏览器会去请求index.php这个文件,正则会匹配/index.php/config.php/%e4/ ,末尾不满足正则表达式的规则,不会被拦截,到rename这,会把%e4,也就是 ä,这个非ASCII码字符丢弃掉,只会拿到config.php,所以highlight_file就成功读取到了config.php文件
得到